PortscanAIThis Snort(TM) preprocessor uses an Artificial Neural Network to detect portscan attempts, additionally presents statistics and graphics in its Web interface. Preprocessor is implemented in ANSI C language and its Web interface in PHP. General workflow scheme is shown in next figure.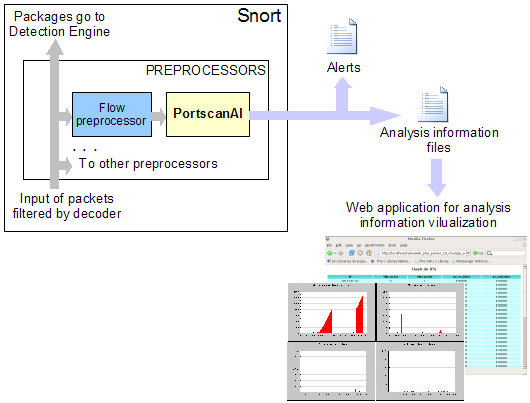 Description: PortscanAI preprocessor takes new flows from Flow preprocessor, looks for portscan activity and if find any, generates an alert in Snort's alert file. Optionally, generates analysis information files to be reviewed by network administrator with help of the Web application. Internal workflow of PortscanAI preprocessor is shown in next figure. 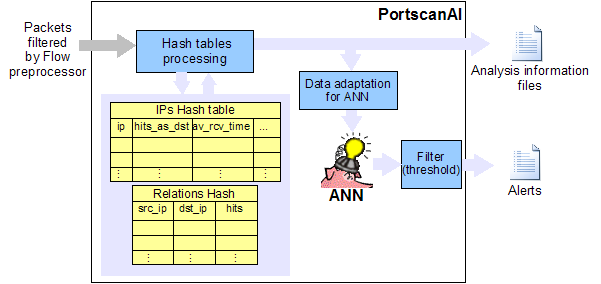 Description: The module of Hash tables processing receives a new flow package and writes in Hash tables important parameters obtained form that package (see Hash tables data). This module optionally creates some files to make graphs about parameters behavior. Data adaptation for ANN (Artificial Neural Network) module, normalizes and makes relations of those parameters to produce the inputs for the ANN (see Inputs of the ANN). This ANN gives a result represented in two float digits between 0 and 1. One digit is the probability of this traffic be normal and the other is the probability of this traffic be a portscan. For example, one result of the ANN could be 20% (0.2) normal traffic and 80% (0.8) portscan. Filter module applies a threshold to ANN result, if result value is more than or less than the threshold, an alert is generated. For example, if normal traffic digit is less than 40% so a portscan alert is generated. This threshold is configurable in the snort.conf file to increase or decrease detection sensitivity. |
||||||||||||
Hash tables dataHash tables have different parameters per each IP address detected in traffic. Following image shows Hash tables with example values as seen in the Web interface.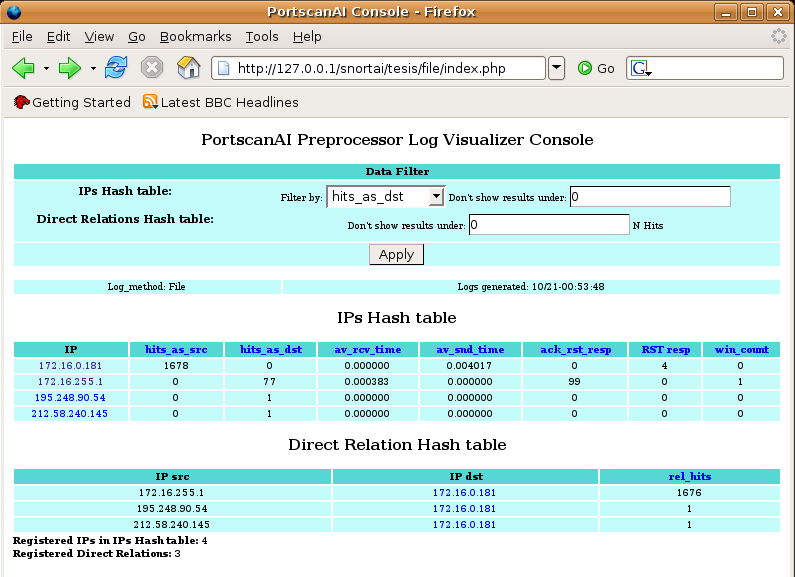 Parameters (fields) of each Hash table are: IP's Hash table:
Direct relation Hash table:
|
||||||||||||
| Download source code from Download section. | ||||||||||||
Project related links:
|